Encryption keys in storage encryption
Here, I describe the commonly used encryption practice you need to understand if you are doing data recovery of anything encrypted.
Message encryption
Let's start with message encryption, which is very simple.
When you are encrypting a message for transmission, you put in three things:
- the plain-text message,
- the encryption key, and
- the encryption algorithm.
Out pops the encrypted message.
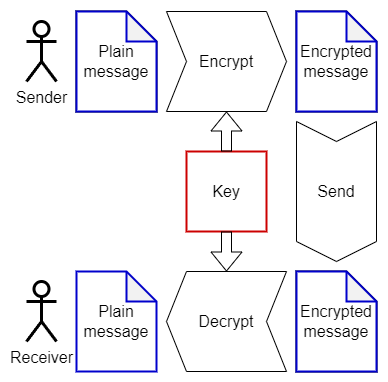
The block diagram of a minimalistic message encryption system.
The key is highlighted in red, and the data is in blue.
Message encryption vs. storage encryption
There is a significant difference between encrypting a message for transmission purposes and encrypting the storage device. The principal difference is this:
- The content of a message does not change once it is encrypted.
The content of a storage device changes all the time, in relatively small parts scattered all over the device.
- Once a message is encrypted and sent, there is no requirement to be able to change the encryption key.
Conversely, the storage system must be able to change the encryption key reasonably fast and often.
Storage encryption implementation
Storage encryption systems use multiple keys to satisfy the two requirements above.
When the encrypted storage is initialized, the system asks the user for a user key.
Then, the system generates a random master key, encrypts the master key with the user key, and stores it somewhere on the media.
The master key is then used to encrypt (and decrypt) the data.
Please note that this scheme requires the user key during initialization.
This requirement is because the master key is never saved unencrypted.
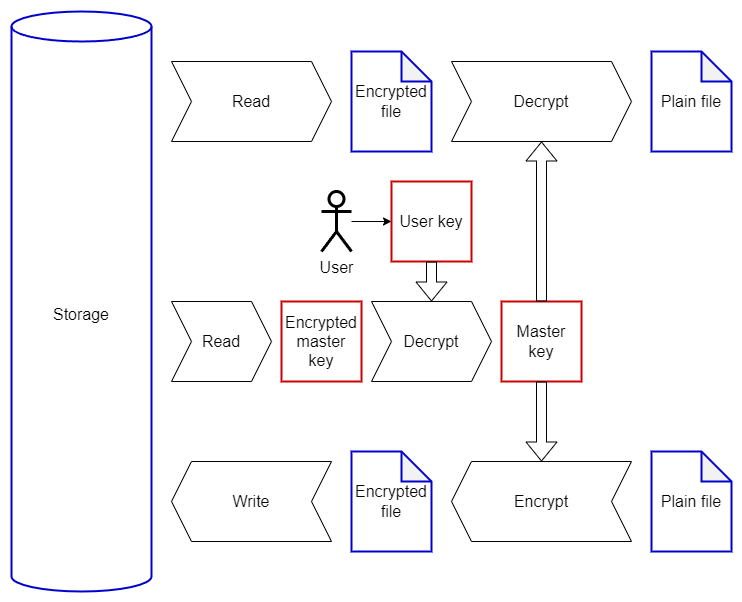
The block diagram of a minimalistic storage encryption system.
Keys are highlighted in red, and data is in blue.
A typical storage system never encrypts the data with the user key. The two-tier key system makes the following possible:
- You can have multiple independent user keys for different users.
-
If you want to change a user key, the only thing you need to re-encrypt is the (small) master key.
A single-key system requires the entire storage to be decrypted and then encrypted with a new key, which takes a long time on larger storage.
-
You can render the entire system securely inaccessible by overwriting the small area where the encrypted master key is stored.
Once the key is overwritten, the rest of the data is unreadable.
However, there are also side effects:
- If the master key is compromised, changing the user key does not resolve the problem.
-
When the key is changed, a CoW system must take special precautions
to make sure no copies of the master key encrypted by the old user key are left lying around as a part of the normal CoW process.
-
In some backup scenarios, you must back up the container with the master key along with the disk image
or whatever other type of backup.
For some reason or other, there are many cases where TrueNAS users end up without their GELI keys backup
during migrations from older to newer TrueNAS systems.
I'm not sure about the specific details, but the procedure appears to be more fragile than expected.
Filed under: Encryption.
Filed under: ZFS.
Created Tuesday, March 14, 2023